Why "Sharding Splits Security" Is a Mid-Curve Argument
“Sharding splits economic security and makes networks weaker.”
This mantra is often parroted in this space without going deeper into the nuances and practicalities of sharding.
It's as if the critics have prematurely dismissed the concept of sharding, without having a comprehensive grasp of what sharding entails and how it works, especially the Radix sharding model!.
In this article, I will explain why the state sharding model of Radix is by far the most secure, more so than monolithic networks such as Solana and far superior to blockchains that attempt to scale with L2s & rollups.
Just a quick heads-up before we get started:
I'm planning to make writing a regular thing.
I'll be sharing updates on all things crypto, tech, and some of my random thoughts.
Social media is full of crypto chatter, and this is a way for me to keep my ideas organized.
So, if you're interested, check out my Substack and follow my ramblings:
What is Economic Security?
In a PoS system, the economic security is derived from the value staked by validators. When someone says that sharding dilutes the security of the network, they imply that the “economic security” of the entire network is split into smaller portions backing each shard.
Firstly, it's important to understand that economic security is not the start and end point when it comes to the overall security of a PoS network, but it is definitely a crucial factor that makes a network difficult to attack. The value of the tokens in a PoS network form the primary means of Sybil defense, so while it is an important factor, there are other aspects to consider, such as the robustness of the consensus mechanism, the decentralization of the network, and the quality of the code.
The greater the economic security backing the network, the better it is.
That being said, let me demystify some widespread misconceptions about economic security.
What Brings Economic Security To a PoS Network?
Apart from speculation on the value of the token, what else exactly causes it to increase in value?
The answer lies in the economic activity that happens within the network.
The value of the native token of a network is directly tied to the level of economic activity happening on the network. We have seen this happening over and over in this industry. We have seen how the ETH token appreciated in value (demand due to the economic activity on-chain plus market speculation) when all those DeFi applications started popping up on Ethereum and driving the on-chain activity.
As more people use the network for transactions, smart contracts, and other activities, the demand for the token increases, driving up its value. This is because the token is required to participate in the network's activities and use dApps.
That’s why metrics like “Fees generated by the networks” matter, because that reflects the level of economic activities on these networks.
The same is true with Solana now. The token price saw its highest price in recent times when the network was at the point of congestion.
(Caveat: Economic activity does not always drive the economic security in a 1:1 ratio, but the growth of economic value backing the network has a strong relationship with the economic activity in that network)
The economic activity in that network is the core factor beyond speculation that drives the value of a native token, which in turn gives economic security to a PoS network.
Also, it's important to understand that the value of these tokens changes with speculation and market demand, so it doesn't remain constant. Considering the fluctuating value of these tokens, one could argue that Solana was 40% less secure two months ago and Ethereum is currently 30% less secure compared to November 2021.
But does it have any real implication on the security of the network on a day-to-day basis? No, because the relative economic security compared to what the attacker may look for to execute a profitable attack is all that matters (which I will explain later).
We now understand what creates economic security and why it's not static.
So, let me explain why we shard a network in the first place and why sharding does not compromise the economic security of a network in any meaningful way.
Why shard in the first place?
It all comes down to the load on the network. Think of it this way - if your blockchain can already handle a high transaction throughput with its current validator set, then you don't need to shard it yet. Sharding comes into play when the network activity and load have grown so much that the single validator set can't keep up anymore, even after optimizing it to the max.
When to Consider Sharding
Only once you've maxed out that single validator set, you consider sharding to split the load across multiple validator pools. But even then, the more throughput you can squeeze out of each shard's validator set, the higher the economic security per shard will be.
Let's say you have a network that is processing 1,000 transactions per second (TPS), and each validator set can process 100. That means you'd need at least 10 shards, and the economic security is split across all of them. But if you optimize your consensus mechanism so each validator set can process 500 TPS , you'd only need 2 shards.
The economic security of each of those 2 shards would be 5 times greater than each of the 10 shards in the first scenario.
Economic Security Increases with Shards in The Network
If the economic activity in that network is the core factor that gives economic security to a PoS network, then, as you split the network into more shards after maxing out the capacity of the current number of validator sets, we can also assume that the economic security of the network is also increasing as more shards are added.
Imagine we have a network processing 1,000 TPS. Such a network is very valuable, as seen with networks like Ethereum, Solana, Hedera, and Avalanche, with billions of dollars of tokens staked in them. These networks support a lot of DeFi activities and have high economic security due to their high activity, opportunity and value.
A similar network that has the capability to shard may choose not to do so initially if it can handle a high throughput within a single shard. This approach maintains its economic security because all activities are concentrated in that one shard, similar to how a monolithic blockchain like Solana operates.
It's all about concentrating as much economic value as possible into as few shards as needed, rather than prematurely sharding and diluting that security across more shards than necessary.
The goal is maximizing throughput while minimizing the sharding required to achieve it.
It's also important to know that a system that adds more shards as needed will have more economic security overall than a monolithic blockchain that can't shard at all, Once that single validator set is saturated, that’s it, it is done and you are relying on Moores law because you’ve hit the cap of demand processing ability and demand = value.
For a deeper understanding of sharding, check out this issue of the newsletter👇
Why Sharding?
Because my 12 years of experimenting and developing various blockchain architectures have shown me that this is the only design choice that scales with demand and guarantees atomic commitment. People often ask me, "Why Sharding instead of rollups or similar technologies like Solana or Sui?" After 12 …
Meaning, a sharded network has the potential to accumulate more economic security than Solana or a system like Ethereum, where most of the economic activity will be happening on rollups and not contributing to economic security at all!
Not only that, if the demand is creating value at a rate greater than the throughput demand is increasing, then after sharding the impact on individual economic security per shard may be very little.
For example, Solana currently has between $30-40B of staked value providing economic security. No one (other than crackpots) is going to suggest that $30B of economic security is insufficient. If the throughput and value increase of Solana was to double, and then we sharded Solana into 2 shards, each shard would then still have $30B of economic security.
A Demand Driven Elastic Sharding Model
So let's break down how a demand-driven elastic sharding model works using the example of the Babylon and Xi'an networks.
Babylon currently has 100 active validators, capable of around 50-100 TPS with the HotStuff consensus mechanism. The update to Xi'an will significantly also invoke a change the core consensus mechanism.
Xi'an will replace HotStuff with Cassandra+Cerberus consensus. This upgrade is expected to dramatically improve performance, allowing validator sets, of sizes over 1000, to process at least 2000 TPS, including swaps and other complex dApps. This substantial increase in throughput will enable Xi’an to handle higher transaction volumes, supporting more complex and demanding applications on the network.
Radix state sharding model uses a fixed shard space of 2^256 shards, which is an astronomically large number, ensuring that the shard space will remain mostly empty and has practically unlimited room for growth.
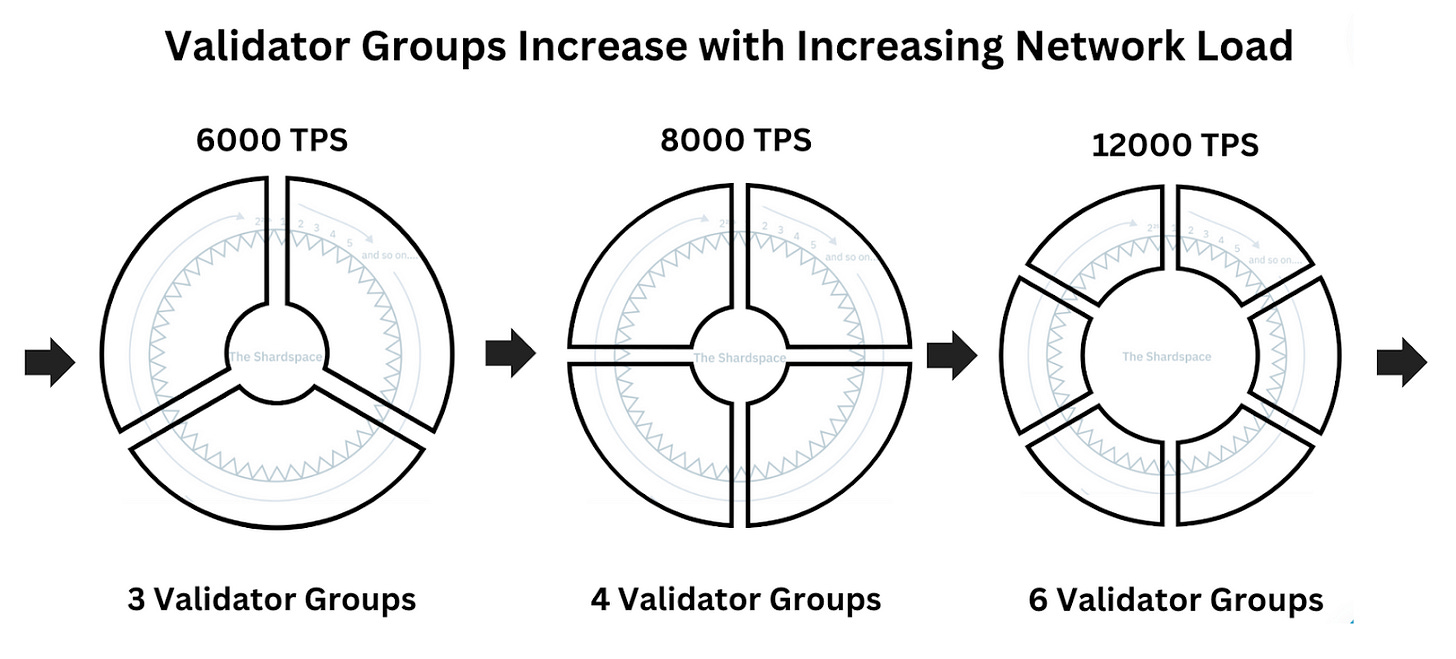
Initially, this fixed shard space will be managed by a single validator set. As demand and throughput on Xi'an grows or shrinks, the network will adjust the number of validator sets..
Initially, there’s no need to shard because the load is manageable. But as transactions increase, the system will decide when to shard, balancing the network’s load and maintaining economic security.
This is How Sharding Happens
So, let’s say the network load hits 2000 TPS, the system might decide to start sharding via adding validator sets and each validator set is responsible for a slice of total shard space. Validators in the network, who are the backbone of the system, will reach a consensus to either increase or decrease the number of validator sets based on the load.
For instance, if the validators see that their load is consistently high, the system may be at full capacity - meaning validators are using nearly all their resources, like CPU and I/O with say just 10% left - then they will propose to increase the quantity of validator sets.
Validators monitor their load and when they reach a point where they’re resource saturated , they signal the network that they think it’s time to consider an adjustment. This is a decentralized decision-making process, so a supermajority (2/3rds) of all validators has to agree. If the majority of validators agree that they’re at their capacity maximum, they proceed with the change, adding more validator sets.
This method ensures that we don’t prematurely shard and end up with too many small validator sets, which would reduce economic security. Validators are expected to have some buffer capacity - enough to handle maybe 2500 - 3000 TPS in short bursts.
Validators also have to be careful not to propose sharding unless it’s really needed. If someone tries to propose a change when there’s plenty of capacity left, other validators can call them out. They can check their own resources, like RAM and hard drive space, and see that the proposer is being unreasonable. Repeated attempts by a validator to propose a change to the quantity of validator sets prematurely is a red flag that they may be malicious or trying to manipulate the system, they can be penalized or removed. This ensures that everyone is playing fair, maintaining the network’s integrity.
Now you might be wondering what happens when economic activity decreases in a system with 10 validator sets. If the economic activity drops by 50%, does that mean the economic security and decentralization of each shard also drop by 50%?
The answer is no. We're creating a flexible system that adjusts based on demand.
When demand increases, the system expands. When demand decreases, the system contracts.
This way, with the state-sharding model developed for Radix, the decentralization of the system increases with demand. There is no cap on how many validators this system can accommodate.
Meaning, in this model, incentivized by raw demand, you can have more validators than systems like Solana or Ethereum.
Even when demand decreases, economic security remains proportional to the number of validator sets.
Elasticity and Adaptability
One of the most important features of Radix’s sharding is its elasticity
If the network load decreases, validators can suggest reducing the number of validator sets.
If the network activity shrinks, validators can also propose to consolidate validator sets , boosting the economic security of the remaining ones.
Validators monitor their load and, when it drops below a certain level, they signal the network to merge validator sets. This requires consensus from the network in the same way as increasing them. If the majority agree, the validator sets are merged.
This approach prevents lots of under-utilized validator sets hanging around, which would be inefficient and make the network vulnerable. Instead, they can reduce them, increasing the security of the remaining ones, ensuring that the network stays robust even as usage drops.
This elastic nature of Radix’s sharding is something many other networks don’t have and state sharding is once again the key. Most other architectures can’t shrink their shards once they’ve been created, which is a real limitation, considering the fact that such models are really diluting the economic security of those shards, making it easier for attackers to target them.
However, it's not all about economic security. The security of a network also depends on the number of validators participating in that network.
Sharding Maximises Decentralization
As I said before, economic security is only a part of what makes a network secure. Ideally, you want to maximize the number of validator nodes a system can accommodate.
Why?
Because the more validators in a system, the harder it becomes for any single malicious actor to gain control. If there are only a handful of validators, it’s much easier for someone with bad intentions to convince a few to join their cause. But with a thousand validators, this task becomes nearly impossible.
Sharding allows the system to add more validators as demand grows. This is unlike Ethereum, where capacity is limited and activity and economic security moves to L2 and L3. It is also different from Solana, where capacity is maxed out and most transactions fail because no more resources can be added to handle the demand.
Sharding Incentivises Decentralization
In a non-sharded system, continually increasing the number of validators means more data for each to process. This will eventually slow everything down. But with sharding, each validator only needs to process the data for its specific area of the shardspace.
When you have many validator sets maintaining the transactions going through the shard space, the entire network is much more decentralized. No single validator set holds all the power. An attacker would need to compromise validators across multiple sets, which is exponentially harder than targeting a single set of validators.
Moreover, low validator requirements and more populated validator sets (as is the case with Cassie) encourages large stakers to operate their own validators. This acts as a deterrent because the adversary must spread their resources thinner and work harder to gain the necessary stake.
The larger the validator set that can be supported per group, the more difficult it becomes for an adversary to control it. This is particularly relevant in the context of delegated stake systems like DPoS.
For instance, in a scenario with 100 validators, if 34 are controlled by an adversary, they can behave favorably for a period to attract stake. Assuming an even distribution and a hypothetical $10 billion stake per shard group, the adversary could access a significant portion of the required stake, making the attack somewhat cheaper.
However, if each process can support 1000 validators or more, there is a much greater opportunity for large stakers to run their own validators rather than paying fees on delegated stake. This forces adversaries to operate more validators and "work harder" to attract the big stakeholders who may prefer to run their own validators.
Simply put, the low validator requirements and increased set size capabilities of the Radix sharding model dramatically enhances the overall decentralization and security of the network.
With more validators spread across many sets, it's harder to perform the activities required for an adversary to take control such as Eclipse attacks.
In an Eclipse attack, the attacker tries to isolate and control the network communication of the target validators. In a highly decentralized, sharded system, the attacker must isolate many more validators across different sets, making such attacks almost impossible. State sharding as developed for Radix adds further headaches because transactions which touch a single validator set are very rare!
Additionally, sharding prevents centralization of power. In a non-sharded system, validators with more resources might dominate because they can handle the heavy data load better. But in a sharded system, even validators with modest resources can participate effectively because they only need to handle a small part of the network’s total data. This inclusivity strengthens the resilience of the whole network.
“Attackers Love Shards”: The Simpleton's Dream
Now let’s get into the most naive argument against the security of sharded networks: as the network is now divided into many shards, you can ‘easily’ attack one single shard compared to attacking a monolithic un-sharded network.
I would now tell you, it’s not as simple as some say. In fact, it is more difficult to attack a sharded network than a monolithic network like Solana.
Let me explain why sharded networks have better security than monolithic Blockchains:
A Sharded Network's Security is not Compromised Just Because it’s Divided into Shards.
Imagine you have a network with 100,000 validators split across 100 sets, each responsible for 1% of the shardspace. Each set, therefore, has 1,000 validators. If someone acquires 0.34% of the overall stake in the network, it doesn't mean they can directly control 34% of a single set and attack it.
Validators are assigned to sets randomly and shuffled around every epoch (which is say 1 day). Let's take validator set 50; every day some validators will relocate to another set, some validators will relocate from another set, and most of them will remain. The next day it happens again, and again. Eventually after a number of epochs, all validators will have cycled through set 50.
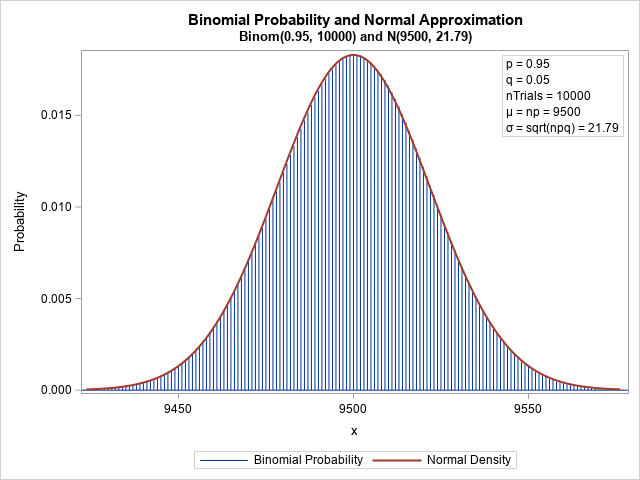
In a network with 100,000 validators, the chance of attacking one shard with just 0.34% of the stake is very very low. The calculation for this probability can be done using a basic binomial distribution.
The calculations would show that an attacker would need to wait for hundreds of thousands of epochs before all their stake is consolidated in one shard.
What the Z-Score Tells Us
The z-score helps us understand how far away a particular value is from the mean in terms of standard deviations.
A z-score of 183 is extremely high. In the context of normal distribution:
A z-score of 2 is already quite rare (only about 2.5% chance).
A z-score of 183 is so far off the charts that the probability is practically zero.
This immense wait time makes such an attack impractical and virtually impossible. And even then, it might not be a validator set you're interested in.
In the best case scenario, you might aim for shard 54 for example, but they all end up in shard 26. In this case, you might cause some liveness issues in that particular area of the shardspace “for the lols” if you're sophisticated enough, but you won't be in control for long.
This means an attacker cannot accurately target a specific shard, as your validators are redistributed in every epoch.
So you might have a brief window, at most one or two epochs, where you could cause some disruption. But the probability trends quickly towards at least one of your validators being shuffled elsewhere, causing you to lose influence on that set.
What if the attacker wants to increase their chances of accumulating enough stake in a set of their choice or reduce the interval of time of their stake consolidating there? Their ONLY option is to acquire a larger percentage of total network stake and spread it around more validators.
The higher a probability of success over a short time window means more stake required. If the attacker wanted to attack validator set 50 tomorrow, they would require at least 34% of all stake!
Similarly if they wanted to attack Solana tomorrow, guess what, they would need at least 34% of all stake!
Additional Security Layers
In sharded networks, transactions between shards require validators from both the sending and receiving shards. When a transaction is initiated from one shard to another, it isn’t just the validator set maintaining the sending shard who are involved. Validators maintaining the receiving shard also need to validate and approve the transaction. This means that no single shard can control the entire transaction process.
So, when a transaction happens between two shards, one sending shard (e.g., shard A) and another receiving shard (e.g., shard B), validators sets maintaining both shards A and B are actively involved in validating and approving the transaction.
For a successful attack, the adversary would need to exert influence over the validator sets in both the originating shard (A) and the destination shard (B). This requirement for influence doubles the challenge compared to systems where only one set of validators is involved.
Additionally, every transaction in Radix's state sharding model includes a randomly selected subset of validators from across the entire network, denoted as set X'. For an attacker, this means they must also have influence over this randomly selected group of validators to potentially manipulate or disrupt a transaction.
To effectively execute an attack, the adversary must therefore control validators in all relevant shards (A, B, and X'). Given that X' is randomly chosen for each transaction, ensuring influence over these sets requires controlling a significant portion of the entire network's validator stake, exceeding 34%.
Even then, the variability introduced by the random selection of validators (X') adds an additional layer of uncertainty, making it exceedingly difficult to guarantee the success of any malicious transaction influence.
Practical Barriers of an Attack
And finally, the practical aspects of an attack:
Attacking a sharded network with high demand, throughput and economic activity is not cheap. It requires a significant amount of money, even acquiring ‘just’ 0.34% of stake in the example above could run into the billions, given the potential economic activity of a network processing 10,000s TPS. If you have $3 billion to launch an attack, there's a chance you could lose it all if the attack doesn't work. If the network finds out you attacked it, even if unsuccessful, it can slash all your stake in the network.
The potential rewards of a successful attack often don't match the risk and cost. If you spend $3 billion, you would probably expect to make at least $4 billion in return. But in reality, there aren't many attacks that can guarantee such high returns.
Even if you can argue that there are ways to acquire significant stake cheaper than the market value, you have to realize that there are no “Zero-Cost Attacks.” Here’s a write-up where I have debunked Anatoly Yakovenko's arguments about such attacks.
So, the profit must be worth the risk of losing everything, including the reputation and market of the business or individual, which can potentially execute so-called “Zero Cost Attacks.”
If you have that kind of money to risk, it’s often more profitable to use it in a positive way within the network. Engaging in beneficial activities might yield better results without the same level of risk.
Final Thoughts
With a sharded system like Radix, you have a setup that accumulates economic security. The more economic activity the system can handle, the stronger its economic security becomes. The Radix sharding model also allows unlimited participation for validators, which maximizes decentralization, unlike systems like Solana or Ethereum. And the best part, this whole process is driven by pure market demand to process more transactions.
And from a security perspective, the state sharding model of Radix that ensures atomic commitment, where transactions occur between multiple shards, it is not enough for an attacker to control a single shard, and even that itself is statistically impossible.
So let me conclude by saying this: the system we are building by leveraging the state sharding model is more resilient and more secure than monolithic blockchains like Solana and systems like Ethereum, which try to drive away economic activity to rollups (which i think that is an absolute madness of a model).
It’s time to put these arguments against sharding security to bed. They were manufactured and cherry-picked by those with their own agendas, to push their own wares because they made the wrong design choices or couldn’t figure out an end to end solution that works.
If you still believe that sharding in general is not a great candidate to address scale, that is of course fine, but I would ask that you don’t fall blindly for the intellectual dishonesty of those with influence.
Hey, if you enjoyed these insights and want to read more articles like this, subscribe to my blog.
I’ll be sharing regular updates on all things crypto, tech, and my random thoughts.
It’s hard to compete with all the crypto noise on social media, and this helps me organize my thoughts better.
So, check out my Substack and follow my ramblings: